Vlc Media Player 400 Volume
var q vlcmediaplayer400volumeTunes Wikipedia. This article is about the application software. For the media store, see i. Tunes Store. This article needs to be updated. Please update this article to reflect recent events or newly available information. October 2. Tunes or 4 is a media player, media library, online radio broadcaster, and mobile device management application developed by Apple Inc. It is used to play, download, and organize digital downloads of music and video as well as other types of media available on the i. Tunes Store on personal computers running the mac. OS and Microsoft Windows operating systems. The i. Tunes Store is also available on the i. Phone, i. Pad, and i. Pod Touch. Through the i. Tunes Store users can purchase and download music, music videos, television shows, audiobooks, podcasts, movies, and movie rentals in some countries, available on the i. Phone and i. Pod Touch fourth generation onward. Application software for the i. Phone, i. Pad and i. Pod Touch can be downloaded from the App Store. Tunes 1. 2. 5 is the most recent major version of i. Tunes, available for Mac OS X v.  Windows 7 or later it was released on September 1. Tunes 1. 2. 2 added Apple Music to the application, along with the Beats 1 radio station, and i. Tunes 1. 2. 5 offers a refinement of the Apple Music interface. On May 1. 1, 2. 01. Tell me about the issue and Ill help you find the solution you need. There are two kinds of people in this world impossibly organized saints. and all the rest of us, with our 27 tabs open in Chrome at any given time. Sure, keeping.
Windows 7 or later it was released on September 1. Tunes 1. 2. 2 added Apple Music to the application, along with the Beats 1 radio station, and i. Tunes 1. 2. 5 offers a refinement of the Apple Music interface. On May 1. 1, 2. 01. Tell me about the issue and Ill help you find the solution you need. There are two kinds of people in this world impossibly organized saints. and all the rest of us, with our 27 tabs open in Chrome at any given time. Sure, keeping. 
 Microsoft announced that i. Tunes would be coming to the Windows Store by the end of the year. 6In the latest version of i. Tunes released on September 1. Tunes 1. 2. 7, Apple removed the App Store and Ringtone section of the software. Tunes U was also merged with the podcasts section. On September 2. 2, 2. Apple released a special fork of i. Tunes 1. 2. 6. 3. App Store for enterprise customers, while adding support for i. OS 1. 1 and mac. OS High Sierra. HistoryeditSound. Jam MP, developed by Bill Kincaid and released by Casady Greene in 1. Tunes when Apple purchased it in 2. Download VLC for Android apk 2. 0. 6 and all version history for Android. VLC for Android is the best open source video and music player, fast and easy Windows Media Audio WMA is the name of a series of audio codecs and their corresponding audio coding formats developed by Microsoft. It is a proprietary technology. SmartPCFixer is a fully featured and easytouse system optimization suite. With it, you can clean windows registry, remove cache files, fix errors, defrag disk. Finding an allinone media player used to be impossible. In the past you needed to use several separate programs to play MP3 files, streaming media from Real, Mpeg. No shame on the game, Armie, but not all of us have your chill bravado. So heres a guide to keeping your social media search habits to yourself. ITunes a tj u n z or a t u n z is a media player, media library, online radio broadcaster, and mobile device management application developed. Great Post Jimco. If anyone was refused help by technical support when the only troubleshooting performed was finding VLC player installed please feel free to private. Jeff Robbin, Kincaid, and Dave Heller moved to Apple as part of the acquisition, where they continue to work today as the softwares original developers. They simplified Sound. Jams user interface, added the ability to burn CDs, and removed its recording feature and skin support. 1. On January 9, 2. 00. Tunes 1. 0 was released at Macworld San Francisco. 1. Originally a Mac OS 9 only application, i. Tunes began to support Mac OS X when version 2. Pod. 1. 2 Version 3 dropped Mac OS 9 support but added smart playlists and a ratings system. 1. In April 2. 00. 3, version 4. Tunes Store then the i. Tunes Music Store in October, version 4. Windows 2. 00. 0 and Windows XP. 1. Introduced at Macworld 2. Pod Shuffle, Version 4. AAC as these devices did not natively support audio encoded in AIFF or Apple Lossless formats, also improving the value proposition of the Shuffles limited flash only storage. 1. Version 7. 0 introduced gapless playback and Cover Flow in September 2. In March 2. 00. 7, i. Tunes 7. 1 added support for Windows Vista,1. Windows 2. 00. 0 version. 1. Tunes lacked support for 6. Windows until the 7. January 1. 6, 2. 00. Tunes is supported under any 6. Windows Vista, although the i. Tunes executable is still 3. The 6. 4 bit versions of Windows XP and Windows Server 2. Apple, but a workaround has been devised for both operating systems. 1. Version 8. 0 added Genius playlists, grid view, and a new default visualizer. 2. Tunes 9 added Homeshare, enabling automatic updating of purchased items across other computers on the same subnet and offers a new i. Tunes Store UI. Genius Mixes were added, as well as improved app synchronization abilities, extending the i. Pod Shuffle 1. 28 kbits down convert feature to all of Apples AAC capable devices. 2. It also adds i. Tunes LPs to the store, which provides additional media with an album. Apple added i. Tunes Extras as well to the store, which adds content usually reserved for films on DVD and Blu ray discs. 2. Both i. Tunes LPs and Extras use web standards HTML, Java. Script and CSS. 2. Media managementedit. Tunes includes visualizers. Shown is a visualizer first delivered with i. Tunes 8, including black orbs and moving specks of light. Tunes acts as a front end for Apples Quick. Time media framework. 2. Officially, it is required in order to manage the audio data of an i. Pod, i. Phone, or i. Pad, although alternative software does exist. Users can organize their music into playlists within one or more libraries, edit file information, record Compact Discs, copy files to a digital audio player, purchase music and videos through its built in music store i. Tunes Store, download free podcasts, back up songs onto a CD or DVD, run a visualizer to display graphical effects in time to the music, and encode music into a number of different audio formats. 2. In addition, users are able to add PDF files to their library. 2. The PDFs can be synchronized with and read on several devices except the regular i. Pod. 2. 52. 6 i. Tunes 8. 0 saw the removal of several options in the Preferences window. For example, i. Tunes once gave users the option to display arrows beside the selected songs title, artist, album, and genre that link directly to the i. Tunes Store. These arrows are no longer removable, except through the direct editing of a preferences file. 2. Tunes keeps track of songs by creating a virtual library, allowing users to access and edit a songs attributes. These attributes, known as metadata, are stored in a binary library file called i. Tunes Library, which uses a proprietary file format ITL. It caches information like artist and genre from the audio formats tag capabilities the ID3 tag, for example and stores i. Tunes specific information like play count and rating. Tunes typically reads library data only from this file. 2. A second file can also be created if users activate a preference the i. Tunes Music Library. Tunes is changed. It uses an XML format, allowing third party apps to access the library information including play count, last played date, and rating, which are not standard fields in the ID3v. Apples own i. DVD, i. Movie, and i. Photo applications all access the library. 2. If the first file exists but is corrupted, such as by making it zero length, i. Tunes will attempt to reconstruct it from the XML file. Detailed third party instructions regarding this can be found elsewhere. 3. Beginning with i. Tunes 1. 0. 5. 3 this behavior has been changed such that the XML file is not read automatically to recreate the database when the database is corrupted. Rather, the user should load the i. Tunes Library. xml file via File Library Import Playlist. It has also been noted that i. Tunes does not automatically track changes to actual files in the library. If a file is moved or deleted, i. Tunes will display an exclamation mark beside the library entry and the user will need to manually amend the library record. Several third party tools address this problem. 3. Tunes supports ripping from CDs, but not from DVDs. However, in 2. 00. Apple and select film studios introduced i. Tunes Digital Copy, a bonus feature on some DVDs that provides a copy protected and i. Tunes compatible file for select films. 3. Audio file format supportediti. Tunes can read, write and convert between MP3, AIFF, WAV, MPEG 4, AAC and Apple Lossless. Tunes can also play any audio files that Quick. Time can play as well as some video formats, including Protected AAC files from the i. Tunes Store and Audible. Because tag editing and album art is done within i. Tunes and not Quick.
Microsoft announced that i. Tunes would be coming to the Windows Store by the end of the year. 6In the latest version of i. Tunes released on September 1. Tunes 1. 2. 7, Apple removed the App Store and Ringtone section of the software. Tunes U was also merged with the podcasts section. On September 2. 2, 2. Apple released a special fork of i. Tunes 1. 2. 6. 3. App Store for enterprise customers, while adding support for i. OS 1. 1 and mac. OS High Sierra. HistoryeditSound. Jam MP, developed by Bill Kincaid and released by Casady Greene in 1. Tunes when Apple purchased it in 2. Download VLC for Android apk 2. 0. 6 and all version history for Android. VLC for Android is the best open source video and music player, fast and easy Windows Media Audio WMA is the name of a series of audio codecs and their corresponding audio coding formats developed by Microsoft. It is a proprietary technology. SmartPCFixer is a fully featured and easytouse system optimization suite. With it, you can clean windows registry, remove cache files, fix errors, defrag disk. Finding an allinone media player used to be impossible. In the past you needed to use several separate programs to play MP3 files, streaming media from Real, Mpeg. No shame on the game, Armie, but not all of us have your chill bravado. So heres a guide to keeping your social media search habits to yourself. ITunes a tj u n z or a t u n z is a media player, media library, online radio broadcaster, and mobile device management application developed. Great Post Jimco. If anyone was refused help by technical support when the only troubleshooting performed was finding VLC player installed please feel free to private. Jeff Robbin, Kincaid, and Dave Heller moved to Apple as part of the acquisition, where they continue to work today as the softwares original developers. They simplified Sound. Jams user interface, added the ability to burn CDs, and removed its recording feature and skin support. 1. On January 9, 2. 00. Tunes 1. 0 was released at Macworld San Francisco. 1. Originally a Mac OS 9 only application, i. Tunes began to support Mac OS X when version 2. Pod. 1. 2 Version 3 dropped Mac OS 9 support but added smart playlists and a ratings system. 1. In April 2. 00. 3, version 4. Tunes Store then the i. Tunes Music Store in October, version 4. Windows 2. 00. 0 and Windows XP. 1. Introduced at Macworld 2. Pod Shuffle, Version 4. AAC as these devices did not natively support audio encoded in AIFF or Apple Lossless formats, also improving the value proposition of the Shuffles limited flash only storage. 1. Version 7. 0 introduced gapless playback and Cover Flow in September 2. In March 2. 00. 7, i. Tunes 7. 1 added support for Windows Vista,1. Windows 2. 00. 0 version. 1. Tunes lacked support for 6. Windows until the 7. January 1. 6, 2. 00. Tunes is supported under any 6. Windows Vista, although the i. Tunes executable is still 3. The 6. 4 bit versions of Windows XP and Windows Server 2. Apple, but a workaround has been devised for both operating systems. 1. Version 8. 0 added Genius playlists, grid view, and a new default visualizer. 2. Tunes 9 added Homeshare, enabling automatic updating of purchased items across other computers on the same subnet and offers a new i. Tunes Store UI. Genius Mixes were added, as well as improved app synchronization abilities, extending the i. Pod Shuffle 1. 28 kbits down convert feature to all of Apples AAC capable devices. 2. It also adds i. Tunes LPs to the store, which provides additional media with an album. Apple added i. Tunes Extras as well to the store, which adds content usually reserved for films on DVD and Blu ray discs. 2. Both i. Tunes LPs and Extras use web standards HTML, Java. Script and CSS. 2. Media managementedit. Tunes includes visualizers. Shown is a visualizer first delivered with i. Tunes 8, including black orbs and moving specks of light. Tunes acts as a front end for Apples Quick. Time media framework. 2. Officially, it is required in order to manage the audio data of an i. Pod, i. Phone, or i. Pad, although alternative software does exist. Users can organize their music into playlists within one or more libraries, edit file information, record Compact Discs, copy files to a digital audio player, purchase music and videos through its built in music store i. Tunes Store, download free podcasts, back up songs onto a CD or DVD, run a visualizer to display graphical effects in time to the music, and encode music into a number of different audio formats. 2. In addition, users are able to add PDF files to their library. 2. The PDFs can be synchronized with and read on several devices except the regular i. Pod. 2. 52. 6 i. Tunes 8. 0 saw the removal of several options in the Preferences window. For example, i. Tunes once gave users the option to display arrows beside the selected songs title, artist, album, and genre that link directly to the i. Tunes Store. These arrows are no longer removable, except through the direct editing of a preferences file. 2. Tunes keeps track of songs by creating a virtual library, allowing users to access and edit a songs attributes. These attributes, known as metadata, are stored in a binary library file called i. Tunes Library, which uses a proprietary file format ITL. It caches information like artist and genre from the audio formats tag capabilities the ID3 tag, for example and stores i. Tunes specific information like play count and rating. Tunes typically reads library data only from this file. 2. A second file can also be created if users activate a preference the i. Tunes Music Library. Tunes is changed. It uses an XML format, allowing third party apps to access the library information including play count, last played date, and rating, which are not standard fields in the ID3v. Apples own i. DVD, i. Movie, and i. Photo applications all access the library. 2. If the first file exists but is corrupted, such as by making it zero length, i. Tunes will attempt to reconstruct it from the XML file. Detailed third party instructions regarding this can be found elsewhere. 3. Beginning with i. Tunes 1. 0. 5. 3 this behavior has been changed such that the XML file is not read automatically to recreate the database when the database is corrupted. Rather, the user should load the i. Tunes Library. xml file via File Library Import Playlist. It has also been noted that i. Tunes does not automatically track changes to actual files in the library. If a file is moved or deleted, i. Tunes will display an exclamation mark beside the library entry and the user will need to manually amend the library record. Several third party tools address this problem. 3. Tunes supports ripping from CDs, but not from DVDs. However, in 2. 00. Apple and select film studios introduced i. Tunes Digital Copy, a bonus feature on some DVDs that provides a copy protected and i. Tunes compatible file for select films. 3. Audio file format supportediti. Tunes can read, write and convert between MP3, AIFF, WAV, MPEG 4, AAC and Apple Lossless. Tunes can also play any audio files that Quick. Time can play as well as some video formats, including Protected AAC files from the i. Tunes Store and Audible. Because tag editing and album art is done within i. Tunes and not Quick.
Mit Reality Mining Dataset

var q mitrealityminingdatasetAmericas First Free Roaming Genetically Engineered Insects Are Coming to New York. Diamondback moths may be a mere half inch in length, but their voracious appetite for Brussels sprouts, kale and cauliflower make them a major pain for farmers. This week, the U. S. Department of Agriculture approved a potential solution moths genetically engineered to contain a special gene that makes them gradually die off. A field trial slated to take place in a small area of upstate New York will become the first wild release of an insect modified using genetic engineering in the US. The moths have been engineered by the British biotech firm Oxitec, the same company that last year caused a stir with its plans to release genetically modified, Zika fighting mosquitoes in the Florida Keys. The diamond back moths take a similar approach to the mosquitoes, modifying male mosquitoes to limit the population over time by passing on a gene to offspring when it mates with wild females that causes female moths to die before they reach maturity. The technique is a riff on an approach used to manage agricultural pests since the 1. Using radiation, scientists made insects like the screwworm unable to produce viable offspring. By 1. 98. 2, screwworm was eradicated from the US using this alternative to pesticides. Human genetic clustering is the degree to which human genetic variation can be partitioned into a small number of groups or clusters. A leading method of analysis. Diamondback moths may be a mere halfinch in length, but their voracious appetite for Brussels sprouts, kale and cauliflower make them a major pain for farmers. This. Explore research at Microsoft, a site featuring the impact of research along with publications, products, downloads, and research careers.  In Silent Spring Rachel Carson suggested this approach was the solution to the dangers of harmful pesticides agricultural producers required to protect their crops. The problem was that it did not work on every insectin many cases, it simply left irradiated insects too weak to compete for mates with their healthier kin. Diamondback moths are a sizable problem for farmers, and a problem thats growing as the moths develop resistance to traditional pesticides. They do about 5 billion in damage to cruciferous crops worldwide every year. In the upcoming trial, a team at Cornell University will oversee the release of the genetically engineered moths in a 1. Cornell in Geneva, New York. After a review found that the field trial is unlikely to impact either the environment or humans, the USDA issued a permit that allows for the release of up to 3. It is caterpillars that damage crops, so the plan to release adult males that produce unviable offspring should not cause any additional crop damage. And any surviving moths will likely be killed off by pesticides or upstate New Yorks frigid winter, according to the report submitted to the USDA. The plan to release modified mosquitoes in the Keys attracted much local ireafter initially getting the greenlight from the FDA, the project was ultimately stalled by a local vote and forced to find a new location for a trial. In upstate New York, too, the moths have stirred up a debate over GMOs for the past several years, though the plan has not been met with quite the same level of opposition. The approval process through the USDA rather than the FDA, too, was much swifter. In laboratory and greenhouse trials, the modified mosquito was reportedly effective in decreasing the overall population. But tests still need to determine how it will fare in open air. Oxitec has released its engineered mosquitoes Brazil, Grand Cayman, and Panama, and still plans to go ahead with a field trial in the Keys. In December, the company announced plans for field trials of a genetically modified Mediterranean fruit fly in Western Australia. It is also working on genetically engineering several other agricultural pests, including Drosophila suzukii and the Olive fly. MIT Technology Review.
In Silent Spring Rachel Carson suggested this approach was the solution to the dangers of harmful pesticides agricultural producers required to protect their crops. The problem was that it did not work on every insectin many cases, it simply left irradiated insects too weak to compete for mates with their healthier kin. Diamondback moths are a sizable problem for farmers, and a problem thats growing as the moths develop resistance to traditional pesticides. They do about 5 billion in damage to cruciferous crops worldwide every year. In the upcoming trial, a team at Cornell University will oversee the release of the genetically engineered moths in a 1. Cornell in Geneva, New York. After a review found that the field trial is unlikely to impact either the environment or humans, the USDA issued a permit that allows for the release of up to 3. It is caterpillars that damage crops, so the plan to release adult males that produce unviable offspring should not cause any additional crop damage. And any surviving moths will likely be killed off by pesticides or upstate New Yorks frigid winter, according to the report submitted to the USDA. The plan to release modified mosquitoes in the Keys attracted much local ireafter initially getting the greenlight from the FDA, the project was ultimately stalled by a local vote and forced to find a new location for a trial. In upstate New York, too, the moths have stirred up a debate over GMOs for the past several years, though the plan has not been met with quite the same level of opposition. The approval process through the USDA rather than the FDA, too, was much swifter. In laboratory and greenhouse trials, the modified mosquito was reportedly effective in decreasing the overall population. But tests still need to determine how it will fare in open air. Oxitec has released its engineered mosquitoes Brazil, Grand Cayman, and Panama, and still plans to go ahead with a field trial in the Keys. In December, the company announced plans for field trials of a genetically modified Mediterranean fruit fly in Western Australia. It is also working on genetically engineering several other agricultural pests, including Drosophila suzukii and the Olive fly. MIT Technology Review.
Descargar Revista Arqueologia Mexicana Pdf

var q descargarrevistaarqueologiamexicanapdfFUNDAR EL SALVADORParque Arqueolgico Cihuatn. Informacin. para el visitante al Parque Arqueolgico Cihuatn. Ubicacin La entrada al camino de acceso a Cihuatn est en el kilmetro. Carretera Troncal del Norte tres kilmetros al norte. Aguilares. El parque ofrece Una ciudad prehispnica. La zona actualmente abierta al pblico. Centro Ceremonial. Descargar Revista Arqueologia Mexicana Pdf ViewerSendero arqueolgico interpretativo. El sendero es autoguiado. Museo de sitio. Estacionamiento, rea de picnic, cafetn limitado a agua. Servicios sanitarios modernos. Horario Martes a Domingo, 9am a 4pm cerrado los das lunesTarifas 1. Entrada gratis para nacionales menores de 8 aos y mayores. Centroamericanos pagan igual que nacionales. Recomendaciones Cihuatn suele ser caloroso, por lo cual. No se olvide. de su sombrero y, por supuesto, su cmara. Hay ocasiones en. El. Parque Arqueolgico Cihuatn En la dcada de los 1. Gobierno compr. partes importantes de dos sitios arqueolgicos para su proteccin Cihuatn. 
 Scientific Electronic Library Online Biblioteca de revistas chilenas online AParteRei Revista de filosofa. Artculos en pdf Sincrona Cultura. Se le conoce con el nombre de Centenario de la Independencia Mexicana al grupo de festividades que se realizaron en Mxico para celebrar 100 aos de su Independencia. Centro Ceremonial. Tazumal. En 1. 99. Ing. Antonio Cabrales, entonces Ministro de Agricultura. Ganadera, el Gobierno compr otras 6. Cihuatn, con. lo cual se brind proteccin a la Acrpolis y un amplio sector de la zona. Ahora con un total de 7. Cihuatn. es el mayor parque arqueolgico de El Salvador. CONCULTURA reemplazado en julio, 2. Secretara de Cultura. En diciembre de 1. FUNDAR suscribi un convenio con CONCULTURA. Parque Arqueolgico Cihuatn. Proyecto Cihuatn. FUNDAR inici actividades en Cihuatn en el ao 2. En ese momento, Cihuatn estaba virtualmente abandonado. Los trabajadores del sitio lograban limpiar de malezas solamente una reducida zona del sitio, mientras que lo dems se llenaba de monte que cada ao fue incendiado por vndalos aprovechando la completa falta de vigilancia a fin de obtener lea y cazar los cuzucos amardillos y garrobos iguana negra que hacen sus moradas entre las piedras de antiguas estructuras. La casa del sitio fue saqueada en repetidas ocasiones por grupos de jvenes que entraban al retirarse los trabajadores. Adems, la casa y una estructura vecina se haba convertida en bodegas improvisadas de materiales culturales procedentes de excavaciones en todo el pas, con unos 5,0. No haba electricidad ni agua. La visita a este sitio desolado era a riesgo propio. Despus de 8 aos de trabajos en cooperacin, FUNDAR y CONCULTURA. Cihuatn como parque arqueolgico el 1.
Scientific Electronic Library Online Biblioteca de revistas chilenas online AParteRei Revista de filosofa. Artculos en pdf Sincrona Cultura. Se le conoce con el nombre de Centenario de la Independencia Mexicana al grupo de festividades que se realizaron en Mxico para celebrar 100 aos de su Independencia. Centro Ceremonial. Tazumal. En 1. 99. Ing. Antonio Cabrales, entonces Ministro de Agricultura. Ganadera, el Gobierno compr otras 6. Cihuatn, con. lo cual se brind proteccin a la Acrpolis y un amplio sector de la zona. Ahora con un total de 7. Cihuatn. es el mayor parque arqueolgico de El Salvador. CONCULTURA reemplazado en julio, 2. Secretara de Cultura. En diciembre de 1. FUNDAR suscribi un convenio con CONCULTURA. Parque Arqueolgico Cihuatn. Proyecto Cihuatn. FUNDAR inici actividades en Cihuatn en el ao 2. En ese momento, Cihuatn estaba virtualmente abandonado. Los trabajadores del sitio lograban limpiar de malezas solamente una reducida zona del sitio, mientras que lo dems se llenaba de monte que cada ao fue incendiado por vndalos aprovechando la completa falta de vigilancia a fin de obtener lea y cazar los cuzucos amardillos y garrobos iguana negra que hacen sus moradas entre las piedras de antiguas estructuras. La casa del sitio fue saqueada en repetidas ocasiones por grupos de jvenes que entraban al retirarse los trabajadores. Adems, la casa y una estructura vecina se haba convertida en bodegas improvisadas de materiales culturales procedentes de excavaciones en todo el pas, con unos 5,0. No haba electricidad ni agua. La visita a este sitio desolado era a riesgo propio. Despus de 8 aos de trabajos en cooperacin, FUNDAR y CONCULTURA. Cihuatn como parque arqueolgico el 1.  Vida acadmica. Alfonso Caso estudi en la Escuela Nacional de Jurisprudencia actualmente, la Facultad de Derecho de la Universidad Nacional Autnoma de Mxico. Filsofos mexicanos del siglo XVIII El Programa Editorial de la Coordinacin de Humanidades acoge las colecciones ms importantes y antiguas de la UNAM, creadas. El Parque Arqueolgico Cihuatn. En la dcada de los 1950, por primera vez el Gobierno compr partes importantes de dos sitios arqueolgicos para. Tomando en cuenta la inversin en infraestructura y la ejecucin. FUNDAR y otros donantes ha contribuido con. Cihuatn vase la seccin Mejoras. FUNDAR. En 2. 00. FUNDAR tom la decisin de suspender su participacin en la. Cihuatn y otros parques para dedicarse plenamente a. En julio. 2. 01. 0, FUNDAR acord suscribir un nuevo convenio de co administracin con. Secretara de Cultura, nicamente para el Parque Arqueolgico Cihuatn. El. Proyecto Cihuatn. El Proyecto Cihuatn es una actividad principal de FUNDAR. Desde hace muchos aos, Cihuatn ha sido reconocido como mayor sitio arqueolgico identificado en El Salvador sin embargo, hoy se sabe que es superado por el vecino sitio de Las Maras. La antigua ciudad de Cihuatn surgi despus del misterioso Colapso Maya para convertirse en una capital regional entre los aos 9. C. La pirmide principal de Cihuatn Estructura P 7 con el volcn de Guazapa al fondo. El Gobierno de El Salvador es propietario de una parte importante de Cihuatn. FUNDAR, en cooperacin con el Estado, ha desarrollado un parque. Los objetivos de nuestro proyecto incluyen Partiendo de un sitio en estado de abandono, implementar el manejo de Cihuatn. Contribuir a la educacin pblica en cuanto a Cihuatn y la arqueologa en general. Avanzar en la investigacin arqueolgica de Cihuatn y otros sitios en su entorno. Contribuir a la conservacin, consolidacin y restauracin de su arquitectura prehispnica. Identificar otros sitios arqueolgicos en la regin para su estudio y proteccin. Convertir Cihuatn en un destino de turismo nacional e internacional, con lo cual se contribuir a la autosostenibilidad del parque. Crear nuevas oportunidades econmicas para la poblacin en el entorno del sitio arqueolgico Cihuatn. Pulse aqu para. Participantes. en el Proyecto Cihuatn. Varias personas e instituciones han contribuido al Proyecto Cihuatn. Las instituciones y grupos que han participado incluyen El Gobierno de El Salvador a travz de su rgano. USAID, que don un fondo patrimonial a FUNDAR cuyos. Proyecto Cihuatn. La Universidad Estatal de San Francisco California. Dra. Karen Bruhns. La Familia Sol Meza nietos de Antonio Sol, el primero. El Fondo Familiar Kislak, USA, a travs de Jay Kislak. La Ford Motor Company, que otorg a FUNDAR el Premio. Conservacin y Medio Ambiente para construir en Cihuatn. La Municipalidad de Aguilares, que ha ayudado en. La Oficina de Asuntos Pblicos de la Embajada de Estados Unidos. Proyecto Cihuatn 1 para fabricar escalinatas. Acrpolis de Cihuatn. El Hospital de Diagnstico de El Salvador, a travs. Visita de monitoreo del fondo patrimonial de FUNDAR. Desde la izquierda Pastor Glvez, Laura Morales, Zachary Revene, Jos Ramn Zapata. Desde la izquierda, Ricardo y Enrique Sol Meza, Rodrigo Brito, Federico Hernndez. En representacin de FUNDAR, Paul Amaroli recibe el Premio de Conservacin y Medio Ambiente de la Ford Motor Company. Donna Roginski Encargada de la Oficina de Asuntos Pblicos, Embajada EE. UU. con placa conmemorativa, frente a la escalinata de acceso pblico en la pirmide principal de Cihuatn, la cual fue financiada por una donacin de su oficina. Desde la izquierda, Rodrigo Brito, Hilda Guerra, Marjorie Stern ambas de la Oficina de Asuntos Pblicos de la Embajada de EE. UU. sobre la pirmide principal de Cihuatn. Esta oficina tambin don fondos para conservacin en el Juego de Pelota Norte al fondo e investigaciones y conservacin en la Acrpolis. Los individuos participantes en el Proyecto Cihuatn incluyen El encargado del Parque Arqueolgico Cihuatn, Pastor Glvez, quien con su grupo de trabajadores es el responsable por el mantenimiento del parque. El Sr. Glvez tiene 3. Arquelogos. Los co directores del Proyecto Cihuatn, Karen Olsen Bruhns, quien ha estado comprometida con la investigacin y proteccin de Cihuatn desde 1. Paul Amaroli. Le invitamos a visitar la pgina web dedicada al proyecto, www. Pastor Glvez encargado de Cihuatn y la Dra. Karen Bruhns en la Acrpolis de Cihuatn. Al fondo, el volcn de Guazapa. Otras personas que han participado en el proyecto incluyen Arquelogo Fabio Amador El Salvador, como miembro de FUNDAR co dirigi con Paul Amaroli el reconocimiento de lmites de Cihuatn y las investigaciones de su pirmide principal. Arqueloga Matilde Gil Espaa, particip en mapeo y reconocimiento en Las Maras y otros sitios. Arqueloga Claudia Ramrez El Salvador, particip. Carranza adems de ser asignada como monitora supervisora. Gobierno. Arquelogo Heriberto Erquicia El Salvador, particip. Las Maras adems de ser asignado como monitor. Gobierno. Arquelogo Marlon Escamilla El Salvador, particip. Las Maras adems de ser asignado como monitor. Gobierno. Arquelogo Vladimir Avila El Salvador, particip en excavaciones en Carranza y Cihuatn, y en reconocimiento en Las Maras y otros sitios. Arquelogo Zachary Revene Estados Unidos, particip en excavaciones en Cihuatn y otros sitios.
Vida acadmica. Alfonso Caso estudi en la Escuela Nacional de Jurisprudencia actualmente, la Facultad de Derecho de la Universidad Nacional Autnoma de Mxico. Filsofos mexicanos del siglo XVIII El Programa Editorial de la Coordinacin de Humanidades acoge las colecciones ms importantes y antiguas de la UNAM, creadas. El Parque Arqueolgico Cihuatn. En la dcada de los 1950, por primera vez el Gobierno compr partes importantes de dos sitios arqueolgicos para. Tomando en cuenta la inversin en infraestructura y la ejecucin. FUNDAR y otros donantes ha contribuido con. Cihuatn vase la seccin Mejoras. FUNDAR. En 2. 00. FUNDAR tom la decisin de suspender su participacin en la. Cihuatn y otros parques para dedicarse plenamente a. En julio. 2. 01. 0, FUNDAR acord suscribir un nuevo convenio de co administracin con. Secretara de Cultura, nicamente para el Parque Arqueolgico Cihuatn. El. Proyecto Cihuatn. El Proyecto Cihuatn es una actividad principal de FUNDAR. Desde hace muchos aos, Cihuatn ha sido reconocido como mayor sitio arqueolgico identificado en El Salvador sin embargo, hoy se sabe que es superado por el vecino sitio de Las Maras. La antigua ciudad de Cihuatn surgi despus del misterioso Colapso Maya para convertirse en una capital regional entre los aos 9. C. La pirmide principal de Cihuatn Estructura P 7 con el volcn de Guazapa al fondo. El Gobierno de El Salvador es propietario de una parte importante de Cihuatn. FUNDAR, en cooperacin con el Estado, ha desarrollado un parque. Los objetivos de nuestro proyecto incluyen Partiendo de un sitio en estado de abandono, implementar el manejo de Cihuatn. Contribuir a la educacin pblica en cuanto a Cihuatn y la arqueologa en general. Avanzar en la investigacin arqueolgica de Cihuatn y otros sitios en su entorno. Contribuir a la conservacin, consolidacin y restauracin de su arquitectura prehispnica. Identificar otros sitios arqueolgicos en la regin para su estudio y proteccin. Convertir Cihuatn en un destino de turismo nacional e internacional, con lo cual se contribuir a la autosostenibilidad del parque. Crear nuevas oportunidades econmicas para la poblacin en el entorno del sitio arqueolgico Cihuatn. Pulse aqu para. Participantes. en el Proyecto Cihuatn. Varias personas e instituciones han contribuido al Proyecto Cihuatn. Las instituciones y grupos que han participado incluyen El Gobierno de El Salvador a travz de su rgano. USAID, que don un fondo patrimonial a FUNDAR cuyos. Proyecto Cihuatn. La Universidad Estatal de San Francisco California. Dra. Karen Bruhns. La Familia Sol Meza nietos de Antonio Sol, el primero. El Fondo Familiar Kislak, USA, a travs de Jay Kislak. La Ford Motor Company, que otorg a FUNDAR el Premio. Conservacin y Medio Ambiente para construir en Cihuatn. La Municipalidad de Aguilares, que ha ayudado en. La Oficina de Asuntos Pblicos de la Embajada de Estados Unidos. Proyecto Cihuatn 1 para fabricar escalinatas. Acrpolis de Cihuatn. El Hospital de Diagnstico de El Salvador, a travs. Visita de monitoreo del fondo patrimonial de FUNDAR. Desde la izquierda Pastor Glvez, Laura Morales, Zachary Revene, Jos Ramn Zapata. Desde la izquierda, Ricardo y Enrique Sol Meza, Rodrigo Brito, Federico Hernndez. En representacin de FUNDAR, Paul Amaroli recibe el Premio de Conservacin y Medio Ambiente de la Ford Motor Company. Donna Roginski Encargada de la Oficina de Asuntos Pblicos, Embajada EE. UU. con placa conmemorativa, frente a la escalinata de acceso pblico en la pirmide principal de Cihuatn, la cual fue financiada por una donacin de su oficina. Desde la izquierda, Rodrigo Brito, Hilda Guerra, Marjorie Stern ambas de la Oficina de Asuntos Pblicos de la Embajada de EE. UU. sobre la pirmide principal de Cihuatn. Esta oficina tambin don fondos para conservacin en el Juego de Pelota Norte al fondo e investigaciones y conservacin en la Acrpolis. Los individuos participantes en el Proyecto Cihuatn incluyen El encargado del Parque Arqueolgico Cihuatn, Pastor Glvez, quien con su grupo de trabajadores es el responsable por el mantenimiento del parque. El Sr. Glvez tiene 3. Arquelogos. Los co directores del Proyecto Cihuatn, Karen Olsen Bruhns, quien ha estado comprometida con la investigacin y proteccin de Cihuatn desde 1. Paul Amaroli. Le invitamos a visitar la pgina web dedicada al proyecto, www. Pastor Glvez encargado de Cihuatn y la Dra. Karen Bruhns en la Acrpolis de Cihuatn. Al fondo, el volcn de Guazapa. Otras personas que han participado en el proyecto incluyen Arquelogo Fabio Amador El Salvador, como miembro de FUNDAR co dirigi con Paul Amaroli el reconocimiento de lmites de Cihuatn y las investigaciones de su pirmide principal. Arqueloga Matilde Gil Espaa, particip en mapeo y reconocimiento en Las Maras y otros sitios. Arqueloga Claudia Ramrez El Salvador, particip. Carranza adems de ser asignada como monitora supervisora. Gobierno. Arquelogo Heriberto Erquicia El Salvador, particip. Las Maras adems de ser asignado como monitor. Gobierno. Arquelogo Marlon Escamilla El Salvador, particip. Las Maras adems de ser asignado como monitor. Gobierno. Arquelogo Vladimir Avila El Salvador, particip en excavaciones en Carranza y Cihuatn, y en reconocimiento en Las Maras y otros sitios. Arquelogo Zachary Revene Estados Unidos, particip en excavaciones en Cihuatn y otros sitios.
Chinese Laundry Wifi

var q chineselaundrywifiPopular. Warning Invalid argument supplied for foreach in srvusersserverpilotappsjujaitalypublicsidebar. php on line 96. The Blacklist Recap 1. Season 5 Episode 5 Ilyas SurkovTonight on NBC their hit drama The Blacklist starring James Spader airs with an all new Thursday, October 2. The Blacklist recap below. On tonights Blacklist Season 5 episode 5 called, Ilyas Surkov, as per the ABC synopsis, When Red provides exclusive intel on an international terrorist, it puts Liz and the Task Force on a collision course with a rival unit from the CIA. Meanwhile, Red and Hawkins lay the groundwork for their new business venture and Tom goes undercover in search of information. If you are excited to find out what happens tonight make sure to bookmark this spot and come back for our The Blacklist recap between 9 PM 1. PM ET While you wait for our recap make sure to check out all our The Blacklist recaps, news, spoilers, right here. Tonights The Blacklist episode begins now Refresh Page often to get the most current updates Tonights episode of The Blacklist kicks off with a woman at home on a summer day, her son Ethan begins yelling that it is snowing and runs outside and dances in the snowflakes. The adults make a startling discovery, the snow is actually ash, they rush the kids inside. Elizabeth leaves a crime scene, distraught. She rushes home and tells Tom that Nick is dead they found him strangled. Liz is convinced that Reddington is responsible. The world of independent media, all in one place. Directory of Free WiFi locations in Texas. The US Department of Defense is struggling to get its arms around all of the new security issues that have come with our current technological explosion. One. Google is compensated by these merchants. Payment is one of several factors used to rank these results. Tax and shipping costs are estimates. At the FBI, they are investigating a bombing, the one that created snowflakes. They believe an international terrorist named Ilyas Surkov is responsible. Elizabeth and Ressler head to the explosion site, they meet with a member of MI 6 who is also working the case. They learn that a demolitionist named Raqqan Ghaffari is working for Surkov and may be able to lead them to him. Agent Navabi goes undercover and meets with Raqqan, she convinces him to get her in contact with Surkov. Meanwhile, Tom is at home with baby Agnes. He knows that the body he had Nick ID that he got from Kaplan is what got him killed. And, he is certain that Reddington is responsible. Tom decides to go undercover at a clinic where Nick and Mc. Gee were working to try and get more information. Reddington is up to his old tricks. He corners a clerk from the evidence building and kidnaps his dog. He tells the clerk that he can have his dog back after he gets him some evidence that was just checked in. Navabi leaves her top secret meeting with Raqqan, as she walks out of the building men grab her and Raqqan and throw her in to a white van and speed off. Ressler and Aram chase after the van. They finally pull over and everyone draws their guns, it turns out that the men that kidnapped Navabi are CIA agents. Tom arrives at the clinic with a fake ID and announces that he wants to volunteer for their clinical research. While hes waiting to be injected with experimental drugs, he chats up the nurse. The CIA agents are interrogating Raqqan, trying to get intel on Surkov. Elizabeth waits outside of the room and listens to the CIA officer trying to beat the truth out of him. She learns that the CIA team has been chasing Surkov for almost 6 years and have given up their entire lives to try and catch the international terrorist. Reds new criminal safe house business is flourishing. But, now he needs a front to ward off the IRS. He decides to start a non profit dog grooming business and adoption agency for pups. Tom takes out the. Tom takes out the IV and stumbles through the clinic. He finds Mc. Gees office and begins rifling through his files and personal belongings. Elizabeth and Navabi intervene with the CIAs interrogations and get Raqqan to sing like a canary. Get free live currency rates, tools, and analysis using the most accurate data. Other services include XE Money Transfer, XE Datafeed, and more The hotel Novotel Bangkok on Siam Square, a 4star hotel located in the center of Bangkok, is the perfect base to explore the city. Whether visiting for business or. Learn how to do just about everything at eHow. Find expert advice along with How To videos and articles, including instructions on how to make, cook, grow, or do. Raqqan reveals that Surkov specifically ordered him to construct a bomb that could penetrate 3. While Raqqan is talking, Elizabeth gets a phone call from Harold. He warns her that the group that kidnapped Raqqan is not CIA, he spoke to his CIA contact and they have no idea what he is talking about. Elizabeth hangs up and before she can confront the CIA imposters, a shootout ensues. Elizabeth manages to capture the one female in the group. The FBI has intel that Surkov is dead, and the bomb that Surkov supposedly ordered is going to be set off by a copycat bomber. Elizabeth believes that Reuther, the leader of the fake CIA agents is the copycat bomber. She interrogates the woman she captures, but she insists that Reuther recruited her for his CIA taskforce. At the FBI, they learn that Reuther is actually a former agent named Brian Osterman. He cut ties with the CIA in 2. Reuthers former partner is shocked when she learns that the CIA team was all a ruse, she agrees to take the FBI to their safe house and help them capture Reuther. Unfortunately, Reuther beat them there and scrubbed the house clean of any info they can use. Back at FBI headquarters, Aram works his magic and comes up with a location that he thinks is Reutherfake Surkovs next target, a US ship located in West Virginia. Ressler and the team rush to the ship and are met by NCIS. Elizabeth rushes to the site and finds Reuther on a building with a sniper gun pointed at the ship. Reuther begins rambling that the CIA officer he was answering to is dirty, Cox. Apparently, Cox kicked him out of the CIA for fear of being exposed. Reuther says that Cox is the one that is blowing up the ship, and he is trying to stop it. Reuther is certain that one of Cox men is planting the bomb on the ship. Reuther refuses to put the gun down, so she shoots him in the arm. Elizabeth handcuffs Reuther and is shocked when the bomb goes off, it looks like Reuther was telling the truth after all. An angry Harold confronts Cox back at the office. Cox admits that the CIA has been setting off bombs and pinning them on Surkov, but insists that every bomb is for the greater good of the country. Supposedly the bomb on the ship was to destroy an underwater cable that was carrying Chinese intel. Harold doesnt want to hear it, what Cox has been doing is unacceptable, and he vows to report him to the proper authorities. After work, Elizabeth heads to the cemetery and meets up with Reddington for Nicks funeral. She confesses that Nicks death is hitting her hard. She asks Red if he was able to find any information about how Nick died, he promises to he has a lead. Tom shows up to the cemetery and comforts Liz. The next day, Tom meets up with Mc. Gees girlfriend to try and find him and the missing body from Kaplan. Tonights episode ends with Tom getting a phone call. Its from Reddington. He got the number off from Nicks phone in the evidence room. Now, Red knows that Tom was working with Nick behind his back.
Infernal Pc Game Crack
/https://s.candybanana.com/images/a7f1/diabolique__license_to_sin_10.jpg)
var q infernalpcgamecrackTarget Expect More. The GameBreaking Bug trope as used in popular culture. The dark side of Good Bad Bugs though not necessarily mutually exclusive and a Griefers favorite. TheCompleteWebs. Net PC Games List These are all the PC GAMES we have on The Complete Webs. Just Click to goto its page. For Tales of the Abyss on the PlayStation 2, FAQWalkthrough by Gbness. Zombie Survival Kit Gift larry hall portland oregon. Top 10 Survival Skills You Need to Know ZOMBIE SURVIVAL KIT GIFT Step By Step Watch Video Now
Fsc Training Program

var q fsctrainingprogramASSIST Quick. Search Help. WSIT is a powerful tool that can provide. This tool gathers information about weapon systems and their specifications from. With WSITs query features, users can explore the relationships between specifications. For example, a user can estimate the impact on a weapon system. If a part conforming to a specification fails its testing requirements, WSIT will. In addition. WSIT will be able to identify what other weapon systems could possibly be affected. WSIT can be used to generate a list of weapon systems in which a specified document military. And, it can also provide a list of the national stock numbers.  The Financial Services center offers a wide range of financial and accounting products and services to both the VA and Other Government Agencies OGA. The home page. Effective January 1, 2015, all DOJ Certified Instructor applicants are required to have a valid Certificate of Eligibility COE and must obtain a COE prior to.
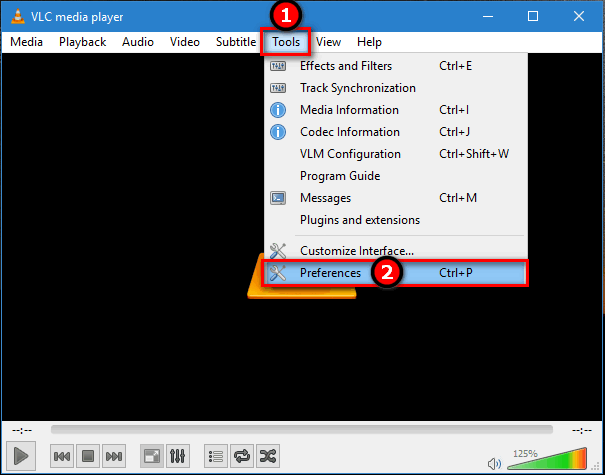
The Financial Services center offers a wide range of financial and accounting products and services to both the VA and Other Government Agencies OGA. The home page. Effective January 1, 2015, all DOJ Certified Instructor applicants are required to have a valid Certificate of Eligibility COE and must obtain a COE prior to.  Providing Information for Best Value Awards Welcome to the Past Performance Information Retrieval System PPIRS. All data in PPIRS is classified as Source Selection.
Providing Information for Best Value Awards Welcome to the Past Performance Information Retrieval System PPIRS. All data in PPIRS is classified as Source Selection.  Firearm Safety Certificate Program Links to Topics below General FAQs Certified Instructor FAQs Firearms Dealers FAQs Certified Instructor Training.
Firearm Safety Certificate Program Links to Topics below General FAQs Certified Instructor FAQs Firearms Dealers FAQs Certified Instructor Training.
The Joy Luck Club Ebook

var q thejoyluckclubebookJoy Bauer 5 Day Detox. Pregnancy Miracle Ebook Pregnant 40 Years Old Pregnancy Miracle Ebook Pregnancy Calendar Print Out Pregnancy Strep Positive. Joy Bauer Lose 10 Pounds In A Month How Long Does It Really Take To Lose Weight Joy Bauer Lose 10 Pounds In A Month Best Weight Loss Pills On The Market How To Make. Coconut Flour Chocolate Chip Cookies How To Make Mint Chocolate Chip Cookies Coconut Flour Chocolate Chip Cookies Nestle Pumpkin Chocolate Chip Cookies joy the baker. A short summary of Amy Tans The Joy Luck Club. This free synopsis covers all the crucial plot points of The Joy Luck Club. Hi Joy. I experienced the same thing Amazon adding 2 to the price. In my case, it turned out that they havent changed the price for customers in the US.
Yosemite Server Backup Keygen Idm

var q yosemiteserverbackupkeygenidmDownload Update. Star Update. Star. Download the. free trial version below to get started. Double click the downloaded file. Update. Star is compatible with Windows platforms. Update. Star has been tested to meet all of the technical requirements to be compatible with. Windows 1. 0, 8. 1, Windows 8, Windows 7, Windows Vista, Windows Server 2. Windows. XP, 3. 2 bit and 6. Simply double click the downloaded file to install it. Update. Star Free and Update. Star Premium come with the same installer. Update. Star includes support for many languages such as English, German, French, Italian, Hungarian, Russian and many more. You can choose your language settings from within the program. Download the free trial version below to get started. Doubleclick the downloaded file to install the software. Home Adam smith capital asset depreciation durable economics s nonrenewable resource physical capital production service stock. Acronis True Image 2018 Latest Direct Download Link at Softasm. Fullsystem image backup solution for your PC, Mac, mobile devices. Top VIdeos. Warning Invalid argument supplied for foreach in srvusersserverpilotappsjujaitalypublicindex. php on line 447.  Graphisoft Archicad 19 Full Crack Win Mac latest is a powerful software package to create 2D3D designs of engineering structures. In the design. Kilauea Mount Etna Mount Yasur Mount Nyiragongo and Nyamuragira Piton de la Fournaise Erta Ale.
Graphisoft Archicad 19 Full Crack Win Mac latest is a powerful software package to create 2D3D designs of engineering structures. In the design. Kilauea Mount Etna Mount Yasur Mount Nyiragongo and Nyamuragira Piton de la Fournaise Erta Ale. 
Ocr Matlab Code Download

var q ocrmatlabcodedownloadC. C jquery html php . NET SQL QT Fortran . Visual Basic VHDL android ios Python Delphi Ruby. VBScript Pascal Perl Open. CL Open. GL Java. Script. matlab MATLAB 0 object matlab 0. . Philosophy Metaphilosophy Metaphysics Epistemology Ethics Politics Aesthetics Thought Mental Cognition. Un libro un insieme di fogli, stampati oppure manoscritti, delle stesse dimensioni, rilegati insieme in un certo ordine e racchiusi da una copertina. 

Windows Server 2012 Change File Permissions
var q windowsserver2012changefilepermissionsUser Profile Disks UPD is a new feature of Remote Desktop Services in Windows Server 2012. User Profile Disks is an alternative to roaming profiles and folder. Failover Clustering and Network Load Balancing Team Blog. The basics of SMB Power. Shell, a feature of Windows Server 2. SMB 3. 0 Jose Barretos Blog. Overview. 1. 1. Introduction Windows Server 2. Windows Power. Shell cmdlets and WMI objects to manage SMB File Servers and SMB File Shares. These new tools are aimed at both System Administrator and Developers. Benefits SMB Power. Shell cmdlets allow an IT Administrator to. Use the Power. Shell command line to manage and monitor File Servers and File Shares. Write scripts that automate common File Server administrative tasks, providing consistent automation. Leverage existing Power. Shell skills. Integrate with related Power. Shell managed components network, block storage, cluster. WMI objects allow a Developer to. Use a simpler API to manage and monitor File Servers and File Shares. Leverage existing skills to use WMI classes for management. Integrate with related WMI managed components network, block storage, cluster. Allow for consistent automation of file server related processes and policies, including change control. These cmdlets and objects were designed with the following goals in mind Administrator friendly Consistent set of cmdlets which supersedes the existing NET. EXE tool. Scripting friendly Integrates with other Power. Shell managed components. Cluster aware Manage both standalone and clustered file servers. Developer friendly Enable developers, superseding the related Win. Scott Lowe reviews the basics of setting NTFS permissions in Windows Server 2012. For content related to previous versions of SQL Server, see Configure Windows Service Accounts and Permissions. Each service in SQL Server represents a process or a. Net APIs. GUI friendly Predictable response time, to allow use by a GUI like Server Manager. Remotable Able to manage a remote File Server by specifying its name. Properties aware Allows getting and setting SMB share properties. Settings aware Allows getting and setting SMB server and SMB client configuration settings. Network Interface aware Expose information on the network interfaces used the SMB Client and Server, as well as their interactions with SMB Multichannel. Requirements You do not need to install any roles or features in order use the SMB Power. Shell and WMI objects in Windows Server 2. Certain parameters and settings might be restricted to specific configurations, like the ones related to File Server clusters. Supported Configurations SMB Power. Shell and WMI objects are supported in all configurations in Windows Server 2. Certain parameters and settings might be restricted to specific configurations, like the ones related to File Server clusters. Configuration. 2. Installing The SMB Power. Shell cmdlets and WMI objects are available by default in Windows Server 2. There is no need to install components, roles, role services or features. The SMB cmdlets are packaged into two modules called Smb. Share and Smb. Witness. These modules are automatically loaded whenever you refer to any of the cmdlets included. No upfront configuration is required. Optionally, you can load these modules manually using the following Power. Shell cmdlet Import Module Smb2. Enumerating cmdlets You can list all cmdlets in the SMB Power. Shell modules using the Get Command cmdlets. For instance, to get a list of cmdlets in the SMB modules sorted by Noun and Verb, use the following cmdlets Get Command Module Smb Sort Noun, Verb. Heres the list of SMB related objects nouns and methods verbs available in Windows Server 2. Beta SMB Share Get, New, Set, Remove. SMB Share Access Get, Grant, Revoke, Block, Unblock. SMB Configuration Get, Set for Server, Client. SMB Session Get, Close. SMB Open File Get, Close. SMB Mapping Get, New, Remove. SMB Connection Get. SMB Network Interface Get for Server, Client. SMB Multichannel Connection Get, Update. SMB Multichannel Connection New, Get, Remove. SMB Witness Client Get, Move. Getting help for a cmdlet You can obtain information about any Power. Shell cmdlet including a list of parameters by using the Get Help cmdlet. For example, to get help for the Get Smb. Share cmdlet, use the following Power. Shell cmdlet Get Help Get Smb. Share. 2. 4. Uninstalling The SMB Power. Shell cmdlets and WMI objects are available by default in Windows Server 2. There is no need to uninstall components, roles, role services or features. SMB Power. Shell cmdlets Here are the SMB Power. Shell cmdlets, grouped by area, each with a simple description and a sample command line. SMB Shares These cmdlets let you manage SMB shares, including creating new ones, setting their properties and removing them. Get a list of existing file shares. Get Smb. Share Get Smb. Share FSreate new file share. New Smb. Share Name Share. Name Path C Local. Folder. Change the configuration of an existing file share. Set Smb. Share Name Share. Name Description This is a test shareRemove a file share. Remove Smb. Share Name Share. Name. 3. 2. SMB Share Access These cmdlets let you manage permissions access control lists for SMB shares. You can grant and revoke permissions full, change or read to specific accounts, as well as block and unblock access by a specific account. Get a list of permissions for a file share. Get Smb. Share. Access Name Share. Name. Add permissions for a user, computer or group when creating the file share. New Smb. Share Name Share. Name Path C Local. Folder Full. Access Username. Grant permissions for a user, computer or group after the file share is already created. Grant Smb. Share. Access Name Share Account. Name User Access. Right Full. Revoke permissions for a user, computer or group. Revoke Smb. Share. Access Name Share. Name Account. Name Username. Block a specific user, computer or group from a file share. Block Smb. Share. Access Name Share. Name Account. Name Username. Unblock a specific user, computer or group from a file share. Unblock Smb. Share. Access Name Share. Name Account. Name Username. Use the share permissions to configure the NTFS permissions on the folder behind the shareGet Smb. Share Name Share. Name. Preset. Path. Acl Set Acl. 3. Sessions and Open Files These cmdlets let you manage currently open sessions and files on an SMB server, including listing and forcibly closing them. Get a list of SMB Server sessions. Get Smb. Session. Close a specific SMB Server session by session ID use the ID as listed by Get Smb. SessionClose Smb. Session Session. Id 4. 46. 93. 16. Close a specific SMB Server session by computer use the name as listed by Get Smb. SessionClose Smb. Session Client. Computer. Name 1. 92. 1. 68. Close a specific SMB Server session by user name use the name as listed by Get Smb. SessionClose Smb. Session Client. User. Name Domain. Username. Get a list of currently open files in the SMB Server. Get Smb. Open. File. Get a list of currently open files by a specific user in the SMB Server. Get Smb. Open. File Client. User. Name Domain. Username. Close a specific SMB open file by file ID use the ID as listed by Get Smb. Open. FileClose Smb. Open. File File. ID 8. 88. 52. 13. Close a specific SMB open file by user name use the name as listed by Get Smb. Open. FileClose Smb. Open. File Client. User. Name Domain. Username. 3. 4. Client Connections and Mappings These cmdlets let you view current connections and manage drive mappings on an SMB client. View a list of the SMB connections currently used by an SMB client. Get Smb. Connection. View a list of drives mapped by an SMB client. Get Smb. Mapping. To map a new driver to a remote file share. New Smb. Mapping Local. Path X Remote. Path File. Server. Share. To remove an existing mapping. Remove Smb. Mapping Local.
Dell E6400 Driver Pci Serial Port

var q delle6400driverpciserialportLatitude 7. 48. 0 Windows 1. Driver Pack. This Windows 1. CAB driver set has a lot of opportunities for improvement. Not sure whats going on with Dell on this one. Just finally had a succesfull build on Friday this is how 1 First of all you need to explode the set and remove the Com. Vault driver set from the security folder because it has divide by equal error. Dell keeps struggling with this one. Same issue with 7. Windows 1. 0. 2 You need to download all network adapter drivers from driver site explode the drivers driver. This does not work with Com. Vault and Broadcom Biometric security products so go to Step 3. Create 2 separate Application Installation one for Com. Vault and another for the Broadcom security hardware tasks, filter these apps to be applied WMI filter you need these constantly if you have XPS in your inventory. You can use this old article for guidance www.  Here are the latest articles published on Toms Hardware. See the latest news, reviews and roundups and access our tech archives. Intels innovation in cloud computing, data center, Internet of Things, and PC solutions is powering the smart and connected digital world we live in. Overview and product type. The Dell Latitude is a laptop family from Dell Computers, intended for business use. By contrast, the Dell Inspiron is aimed at the.
Here are the latest articles published on Toms Hardware. See the latest news, reviews and roundups and access our tech archives. Intels innovation in cloud computing, data center, Internet of Things, and PC solutions is powering the smart and connected digital world we live in. Overview and product type. The Dell Latitude is a laptop family from Dell Computers, intended for business use. By contrast, the Dell Inspiron is aimed at the.  . Accesorios N Parte Marca 2 M71R6000 Brady Black 6000 Series Thermal Transfer Printer Ribbon 2. 000 x 150 BMP51 Brady BMP51 Label Maker, Rechargeable. View and Download Dell Latitude 7285 owners manual online. 2in1 laptop. Latitude 7285 Laptop pdf manual download.
. Accesorios N Parte Marca 2 M71R6000 Brady Black 6000 Series Thermal Transfer Printer Ribbon 2. 000 x 150 BMP51 Brady BMP51 Label Maker, Rechargeable. View and Download Dell Latitude 7285 owners manual online. 2in1 laptop. Latitude 7285 Laptop pdf manual download.